43 aws best practices
Best practices to create & organize Terraform code for AWS Modules folder contains terraform modules inherently related to the project. Modules are powerful because they make code more readable. S3 as the backend for storing tfstate file. This state file ... aws.amazon.com › architecture › security-identitySecurity, Identity & Compliance | AWS Architecture Center Best Practices for Security, Identity, & Compliance Learn how to meet your security and compliance goals using AWS infrastructure and services. To learn current AWS recommendations and strategies to use when designing cloud architectures with security in mind, see the Security Pillar - AWS Well-Architected Framework .
Top 10 security best practices for securing data in Amazon S3 Web02.09.2021 · The controls contain best practices from across multiple AWS services, including S3. We recommend you enable the AWS Foundational Security Best Practices as it includes the following detective controls for S3 and IAM: IAM.1: IAM policies should not allow full “*” administrative privileges. S3.1: Block Public Access setting should be enabled
Aws best practices
Apache Spark: Architecture, Best Practices, and Alternatives 5 Apache Spark Alternatives. 1. Apache Hadoop. Apache Hadoop is a framework that enables distributed processing of large data sets on clusters of computers, using a simple programming model. The framework is designed to scale from a single server to thousands, each providing local compute and storage. 11 AWS Well-Architected Framework Best Practices - CLIMB The AWS Well-Architected Framework is a set of best practices that can help organizations design and build secure, high-performing, resilient, and efficient cloud architectures. It provides a consistent approach for customers and partners to evaluate architectures, and implement designs that will scale over time. 10 MongoDB AWS Best Practices - CLIMB In this article, we will discuss 10 MongoDB AWS best practices that will help you get the most out of your MongoDB deployment on AWS. We will cover topics such as security, scalability, and performance optimization. 1. Use Amazon EBS volumes for your MongoDB data
Aws best practices. Introduction - EKS Best Practices Guides - GitHub Pages WebWelcome to the EKS Best Practices Guides. The primary goal of this project is to offer a set of best practices for day 2 operations for Amazon EKS. We elected to publish this guidance to GitHub so we could iterate quickly, provide timely and effective recommendations for variety of concerns, and easily incorporate suggestions from the broader community. AWS Amplify User Authentication and Best Practices for iOS app AWS Amplify User Authentication and Best Practices for iOS app. Hi all, So I just stumbled across AWS Amplify a few days ago and I love the Authentication process and I have started to transition my app. So the question that I have, is that I am looking to implement a logic structure similar to this: - Manual Signup. - Signup using Google. Best Practices for AWS Organizations Service Control Policies in a ... Web04.02.2022 · AWS financial services industry (FSI) customers often seek guidance on how to set up their AWS environment and accounts for best results. AWS has created a unified set of recommendations, called the multi-account strategy, to help customers like you make the best use of your AWS resources.In this blog, we provide a representative … Best practices for AWS Organizations - AWS Organizations Best practices for AWS Organizations Best practices for the management account Best practices for member accounts Creating and managing an organization Managing accounts Managing OUs Managing policies Tagging resources Using other AWS services Security AWS Organizations reference Troubleshooting AWS Organizations Making HTTP Query requests
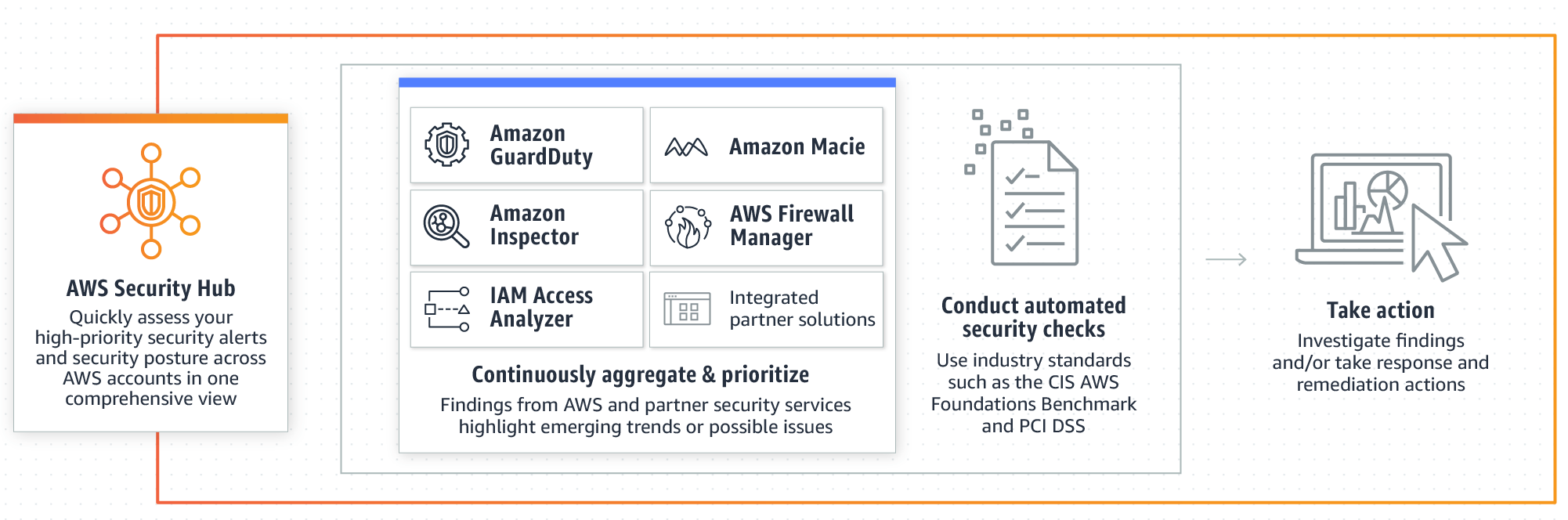
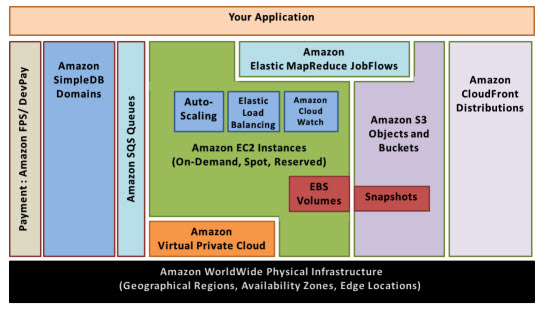
docs.aws.amazon.com › IAM › latestSecurity best practices in IAM - AWS Identity and Access ... Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide. Security best practices for Amazon S3 WebEnable AWS Config. Several of the best practices listed in this topic suggest creating AWS Config rules. AWS Config enables you to assess, audit, and evaluate the configurations of your AWS resources. AWS Config monitors resource configurations, allowing you to evaluate the recorded configurations against the desired secure configurations. Using … Getting Started: Follow Security Best Practices as You Configure Your ... To manage and control access and permissions to your AWS resources, use AWS Identity and Access Management (IAM) to create users, groups, and roles. When you create an IAM user, group, or role, it can access only the AWS resources to which you explicitly grant permissions, which is also known as least privilege. PDF Architecting for the loud Amazon Web Services - Architecting for the Cloud: AWS Best Practices Page 5 Design Principles The AWS Cloud includes many design patterns and architectural options that you can apply to a wide variety of use cases. Some key design principles of the AWS Cloud include scalability, disposable resources, automation, loose coupling managed services
aws.amazon.com › blogs › computeMust-know best practices for Amazon EBS encryption | AWS ... Jul 15, 2020 · This blog post covers common encryption workflows on Amazon EBS. Examples of these workflows are: setting up permissions policies, creating encrypted EBS volumes, running Amazon EC2 instances, taking snapshots, and sharing your encrypted data using customer-managed CMK. Introduction Amazon Elastic Block Store (Amazon EBS) service provides high-performance block-level storage volumes for Amazon ... docs.aws.amazon.com › lambda › latestBest practices for working with AWS Lambda functions Best practices for using AWS Lambda. REPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB Validate your Pull Requests with AWS CDK - linkedin.com Using what AWS refers to as Layer 2 constructs, gives us the advantage of providing best practices with things like, least privileged access. For example, due to the level of abstraction provided ... Data Lake best practices in AWS - Nordcloud Best practices for utilizing a data lake optimized for performance, security and data processing were discussed during the AWS Data Lake Formation session at AWS re:Invent 2018. The session was split up into three main categories: Ingestion, Organisation and Preparation of data for the data lake. Your current bottleneck may lie in all or any of ...
10 Amazon AWS Best Practices - CLIMB However, it is important to use AWS in the right way to ensure that your applications are secure and perform optimally. In this article, we will discuss 10 best practices for using AWS that will help you get the most out of the platform. 1. Use AWS CloudFormation. CloudFormation is a service that allows you to create and manage AWS resources in ...
aws.amazon.com › blogs › mtAWS Config best practices | AWS Cloud Operations & Migrations ... Apr 01, 2020 · AWS Config is a service that maintains a configuration history of your AWS resources and evaluates the configuration against best practices and your internal policies. You can use this information for operational troubleshooting, audit, and compliance use cases. In this blog post, I share best practices on how to use AWS Config as a tool […]
AWS Best Practices: five key approaches - Cloud Academy AWS Best Practices: backup a lot and test your recovery resources before you need them With all your AWS credentials protected and your applications secured you should be sleeping better at night. Now it's time to start thinking about a backup and recovery plan. Here are some things that should be part of any robust backup plan.
AWS CloudFormation Security: 8 Best Practices - Cycode In order to secure this tool, security best practices for AWS CloudFormation should be adhered to as misconfigurations are amplified within IaC environments. We recommend the following to help mitigate risk: 1. Ensure consistent governance through AWS CloudFormation Stack policies. A stack policy is a JSON document that describes what update ...
AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices AWS Whitepaper Welcome AWS Security Best Practices PDF RSS Notice: This whitepaper has been archived. For the latest technical information on Security and Compliance, see .
AWS CloudFormation best practices - AWS CloudFormation WebBest practices are recommendations that can help you use AWS CloudFormation more effectively and securely throughout its entire workflow. Learn how to plan and organize your stacks, create templates that describe your resources and the software applications that run on them, and manage your stacks and their resources.
docs.aws.amazon.com › best-practicesBest practices for AWS accounts - AWS Account Management Best practices for managing AWS access keys Javascript is disabled or is unavailable in your browser. To use the Amazon Web Services Documentation, Javascript must be enabled.
AWS Well-Architected Best Practices | Classroom Training | AWS The AWS Well-Architected Best Practices course will help you learn a consistent approach to evaluate architectures and implement designs from a live instructor. You'll learn how to use the Well-Architected Review process and the AWS Well-Architected Tool to conduct reviews to identify high risk issues (HRIs).
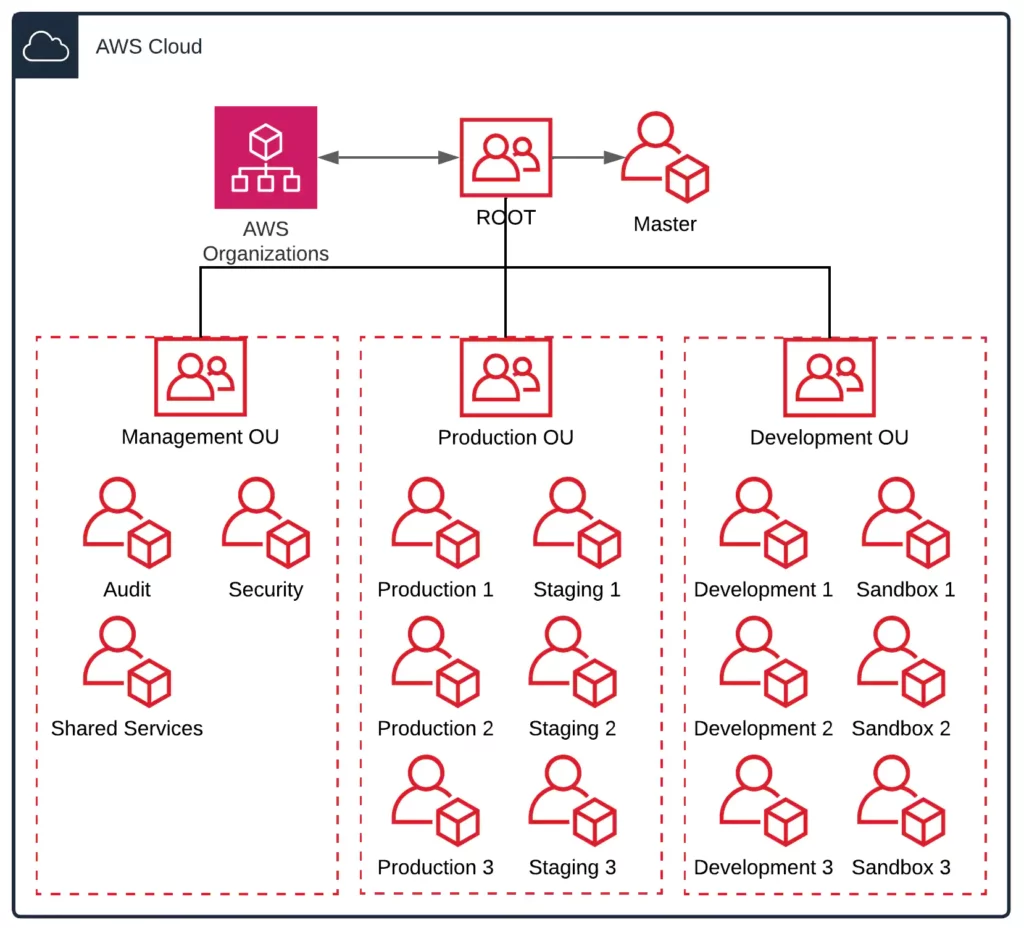
Establishing your best practice AWS environment AWS recommends that you start with security and infrastructure in mind. Most businesses have centralized teams that serve the entire organization for those needs. As such, we recommend creating a set of foundational OUs for these specific functions: Infrastructure: Used for shared infrastructure services such as networking and IT services.
AWS SYSTEM ADMINISTRATION : BEST PRACTICES FOR SYSADMINS IN By Mike ... This comprehensive guide shows developers and system administrators how to configure and manage AWS services including EC2, CloudFormation, Elastic Load Balancing, S3, and Route 53. Sysadms will learn will learn to automate their favorite tools and processes; developers will pick up enough ops knowledge to build a robust and resilient AWS ...
How to get best price performance from your Amazon Redshift Data ... General Amazon Redshift performance tuning best practices are applicable to data sharing deployment. Make sure that your deployment follows these best practices. There numerous data sharing specific best practices that you should follow to make sure that you maximize the performance. Refer to this post for more details. Summary
Best practices for working with AWS Lambda functions WebThe AWS Lambda execution environment contains a number of libraries such as the AWS SDK for the Node.js and Python runtimes (a full list can be found here: Lambda runtimes). To enable the latest set of features and security updates, Lambda will periodically update these libraries. These updates may introduce subtle changes to the behavior of your …
15 AWS Security Best Practices | NETdepot.com AWS Security Best Practices to Keep Your Systems Safe. The cloud can be a dangerous place. But by following these our AWS security best practices, you can make sure that your systems are as protected as possible. Make sure that you have security on all layers of your system, and only provide users the access they require. Perhaps most ...
AWS Identity and Access Management Best Practices AWS Identity and Access Management Best Practices IAM Best Practices Use temporary credentials Require MFA Rotate access keys regularly Safeguard your root user credentials Grant least privilege Use IAM Access Analyzer Set permissions guardrails Delegate permissions management
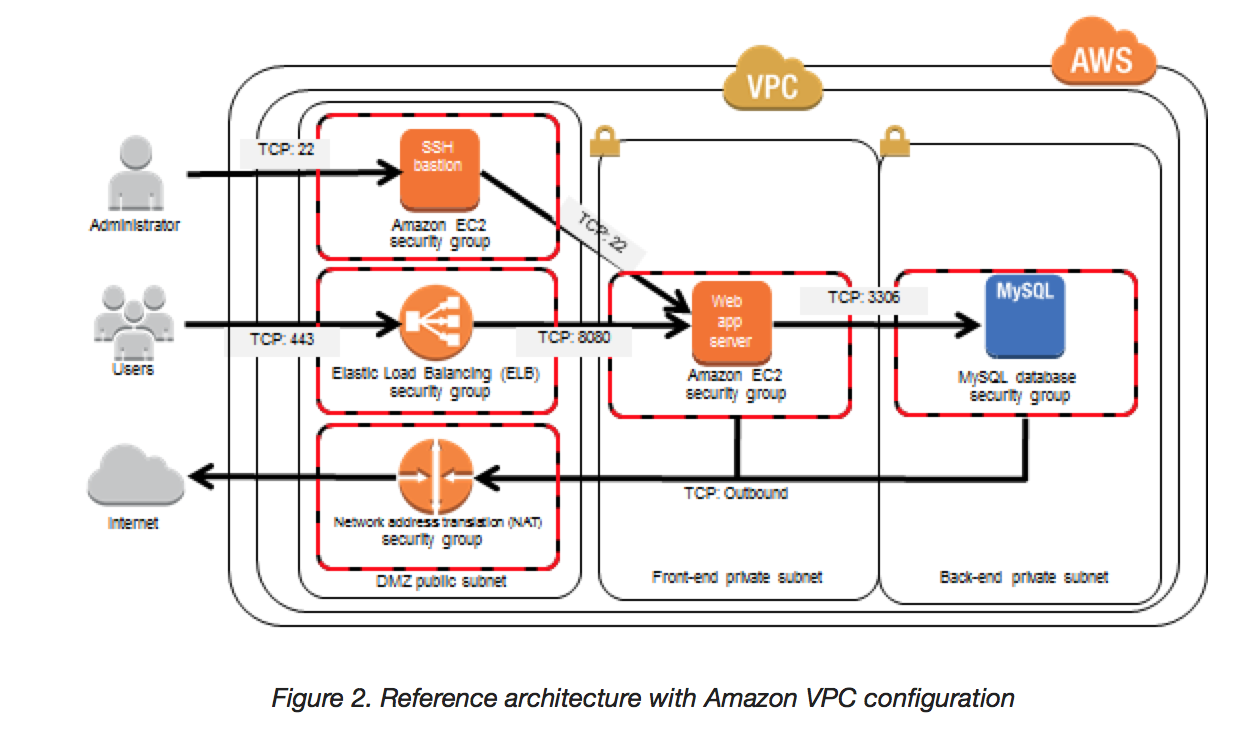
AWS Security Best Practices WebAWS. See Security Best Practices in IAM for more information. Regions, Availability Zones, and Endpoints You should also be familiar with regions, Availability Zones, and endpoints, which are components of the AWS secure global infrastructure. Use AWS regions to manage network latency and regulatory compliance. When you store data in a …
Security Best Practices for AWS WAF - AWS Config Security Best Practices for AWS WAF Example Templates with Remediation Action Custom Conformance Pack Viewing Compliance Data in the Conformance Packs Dashboard Deploying a Conformance Pack (Console) Deploying a Conformance Pack (AWS CLI) Managing Conformance Packs (API) Managing Conformance Packs Across all Accounts in Your Organization
Best practices for Amazon EC2 - Amazon Elastic Compute Cloud How the AWS binary blob is created Find a Linux AMI Shared AMIs Find shared AMIs Make an AMI public Share an AMI with organizations or OUs Share an AMI with specific AWS accounts Use bookmarks Guidelines for shared Linux AMIs Paid AMIs AMI lifecycle Create an AMI Create an Amazon EBS-backed Linux AMI Create an instance store-backed Linux AMI
VMware Tanzu and AWS Accelerate Apps: Key Takeaways from AWS re:Invent 2022 After a successful AWS re:Invent 2022, VMware Tanzu and AWS continue to be in alignment in providing customers with the DevOps tools they need. Here are the key takeaways from the event. ... Best practices enabled by technology are key to customer success . Containers can proliferate very quickly, and at VMware, we have seen this time and time ...
aws.amazon.com › blogs › big-dataTop 8 Best Practices for High-Performance ETL Processing ... Jan 26, 2018 · The AWS Lambda Utility Runner runs a subset of these scripts on a scheduled basis, allowing you to automate much of monitoring of your ETL processes. Example ETL process. The following ETL process reinforces some of the best practices discussed in this post.
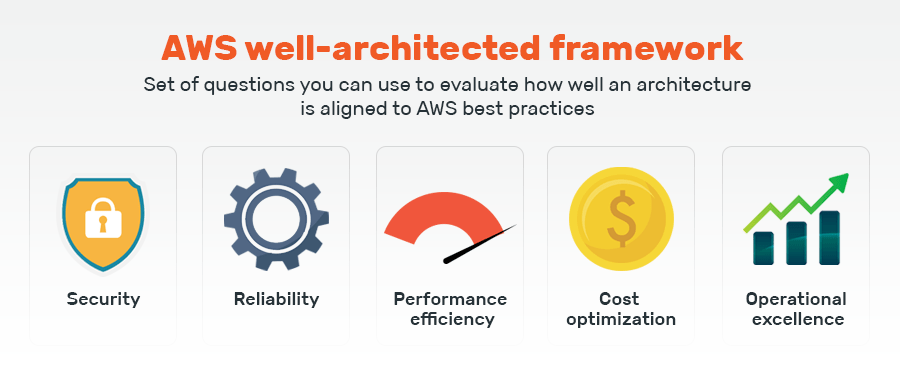
AWS Best Practices for Beginners - Career Karma AWS Best Practices and Guidelines FAQ What are the six pillars of AWS? The six pillars of AWS are sustainability, cost optimization, performance efficiency, reliability, security, and operational excellence. These pillars describe the concepts, principles, and best practices used in designing by architects to onset workloads on the cloud.
Best practices for AWS Budgets - AWS Cost Management Best practices for controlling access to AWS Budgets To allow IAM users to create budgets in the AWS Billing and Cost Management console, you must also allow IAM users to do the following: View your billing information Create Amazon CloudWatch alarms Create Amazon Simple Notification Service (Amazon SNS) notifications
Best practices for AWS accounts - AWS Account Management WebBest practices for AWS accounts. This section describes best practices that we recommend that you follow with your AWS accounts. They are arranged in the following categories: Topics. Best practices to protect your account's root user; Best practices for managing AWS access keys ; Document Conventions. Example SCPs. Root user. This …
Best practice recommendations - Application Pattern Orchestrator on AWS Mono-repo. There are two strategies for managing the codebase in a repository: Mono-repo and Multi-repo. From this solution's perspective we recommend using the mono-repo strategy for patterns. The main reason for recommending mono-repo for patterns code repository is because of the AWS resource limits in an AWS account.
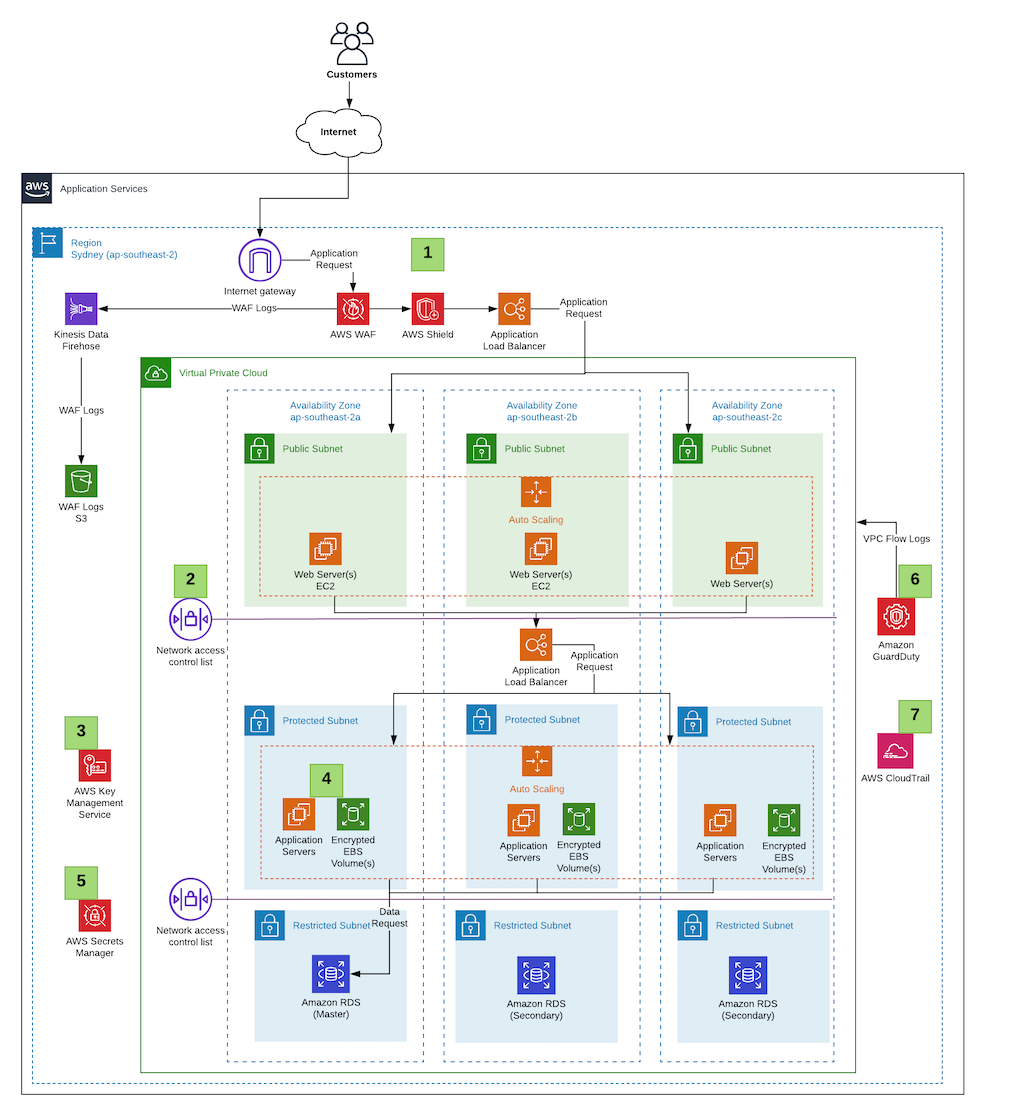
PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 2 Know the AWS Shared Responsibility Model Amazon Web Services provides a secure global infrastructure and services in the cloud. You can build your systems using AWS as the foundation, and architect an ISMS that takes advantage of AWS features.
Security best practices in IAM - AWS Identity and Access … Web14.07.2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
AWS Well-Architected - Build secure, efficient cloud applications AWS Well-Architected Partner Program members have in-depth training on the AWS Well-Architected Framework, and are empowered to implement best practices, measure workload states, and make improvements where required. Customers engaged with these partners see significant cost savings, improved application performance, and reduced security risks.
Establishing your best practice AWS environment WebThe framework described on this page represents AWS best practices that you should use as a starting point for your AWS journey. To get started, refer to the AWS Organizations Getting Started Guide to build your own multi-account AWS environment. Alternatively, you can use AWS Control Tower to help you quickly set up a secure initial AWS environment …
Introduction - EKS Best Practices Guides - GitHub Pages Best Practices for Cluster Autoscaling: karpenter, cluster-autoscaler Best Practices for Running Windows Containers Best Practices for Networking In the future we will be publishing best practices guidance for performance, cost optimization, and operational excellence. Contributing We encourage you to contribute to these guides.
10 MongoDB AWS Best Practices - CLIMB In this article, we will discuss 10 MongoDB AWS best practices that will help you get the most out of your MongoDB deployment on AWS. We will cover topics such as security, scalability, and performance optimization. 1. Use Amazon EBS volumes for your MongoDB data
11 AWS Well-Architected Framework Best Practices - CLIMB The AWS Well-Architected Framework is a set of best practices that can help organizations design and build secure, high-performing, resilient, and efficient cloud architectures. It provides a consistent approach for customers and partners to evaluate architectures, and implement designs that will scale over time.
Apache Spark: Architecture, Best Practices, and Alternatives 5 Apache Spark Alternatives. 1. Apache Hadoop. Apache Hadoop is a framework that enables distributed processing of large data sets on clusters of computers, using a simple programming model. The framework is designed to scale from a single server to thousands, each providing local compute and storage.






.jpg?ixlib=gatsbyFP&auto=compress%2Cformat&fit=max&q=50)


















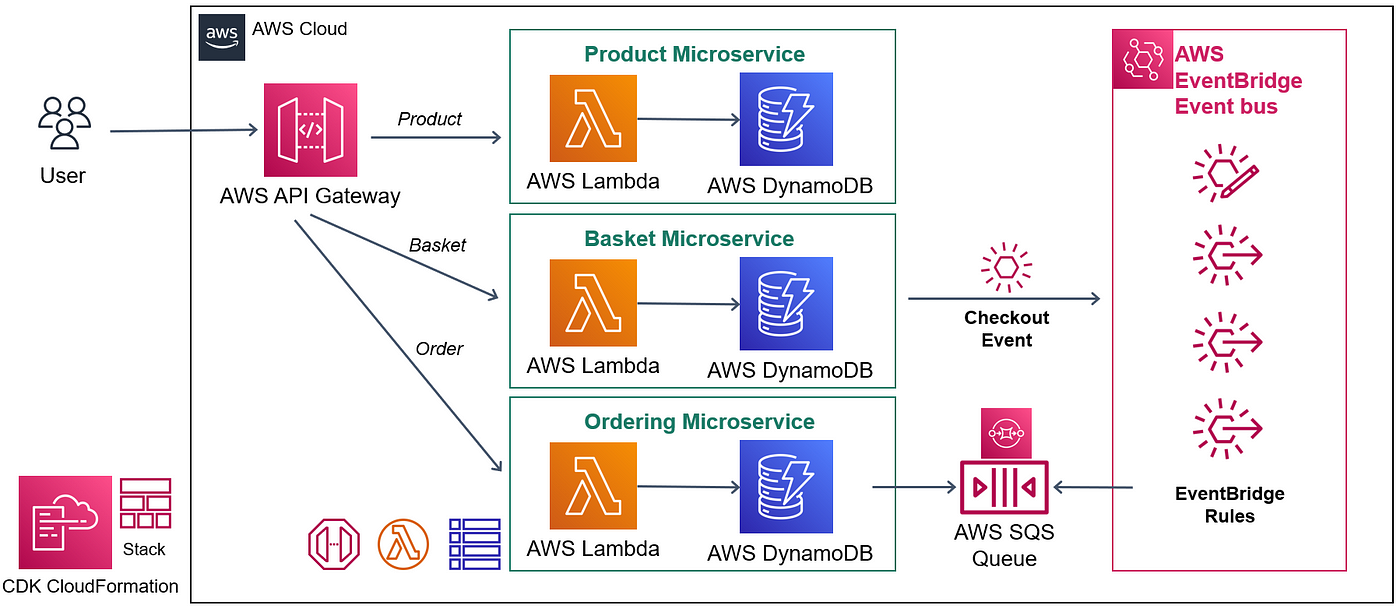

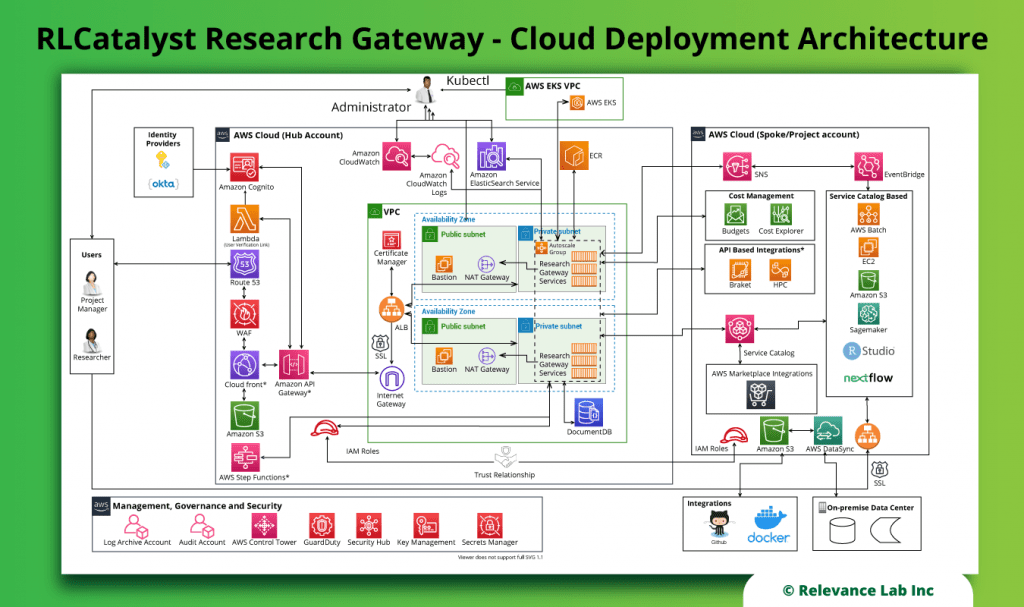


0 Response to "43 aws best practices"
Post a Comment